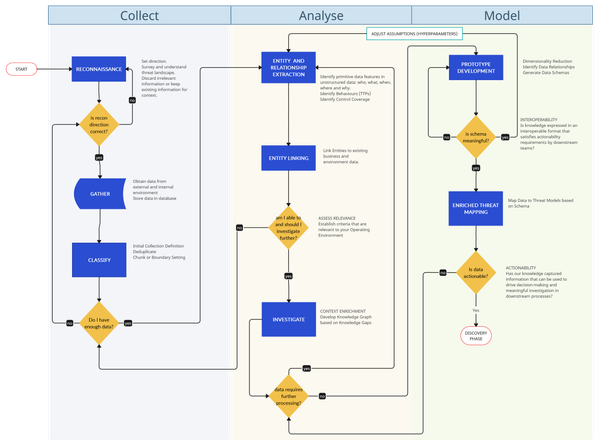
What if your cybersecurity data pipeline functioned like a Git repository, with each team acting as a branch, merging their insights and actions into a "main" pipeline to drive real-world impact? Join me on this "Git-inspired" approach to scalable cyber operations.

Diego Perez
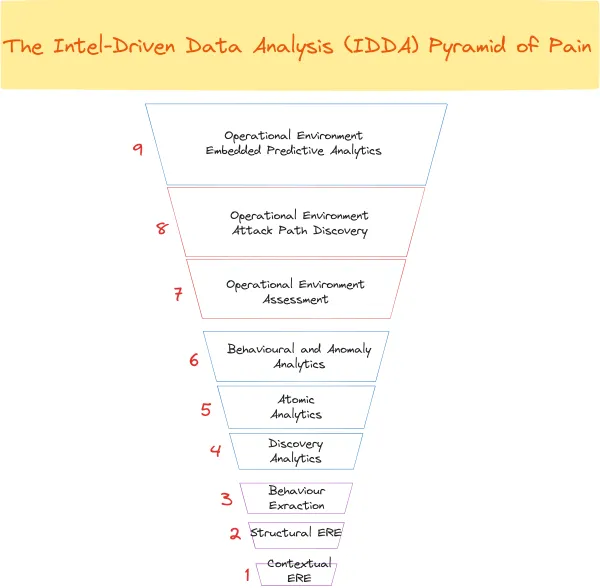
Or should we say a Intel-Driven Data Analysis Pyramid of Pain?
Today, let me start with a bit of confession time: my quest to build an "Active Defense" framework has led me down a rabbit hole of epic proportions even the wisest tech oracles wouldn't have predicted 🐇🕳️🔮.
A simple pondering of questions about the shortsighted views around
In my last post I introduced the RIDE (R1D3) Framework for Active Defence. I outlined there the four basic phases of an active defence pipeline: Research, Discovery, Disruption and Development. In this article, I will describe the first phase (the R in R1D3) in detail. I've scheduled this
Hello my fellow cyberscouts, I have plenty of news to share with you and I need your help today!
Warning: there are some words in this email, but I promise it's a VERY short one. Strings are everywhere my dude/dudette.
* I am changing domains soon, going back
I see a lot of people trying to make sense of the roles they occupy in the cyber defence world. Asking yourself these questions is a good thing to do, primarily because the world's needs advance at a faster pace than our structures can adapt to it. Let&