Understanding Active Cyber Defence Operations
As you all know, I've been talking about Active Defence for quite a while, working hard to make sense of the problem space and bring some order to the concepts that haunt this thing we call "threat intel-led cyber defence" or "proactive cyber defence".
But what is Active Defence Operations after all?
The Active Cyber Defence Matrix
Active Defence Operations represents a fundamental paradigm shift in security, moving away from reactive approaches that inadvertently concede the initiative and tempo of engagement to adversaries.
Traditional security often lacks the dimension of engagement; Active Defence, in contrast, is rooted in the understanding that engagement with cyber threats is inevitable, and strategic advantage is gained through positional defence.
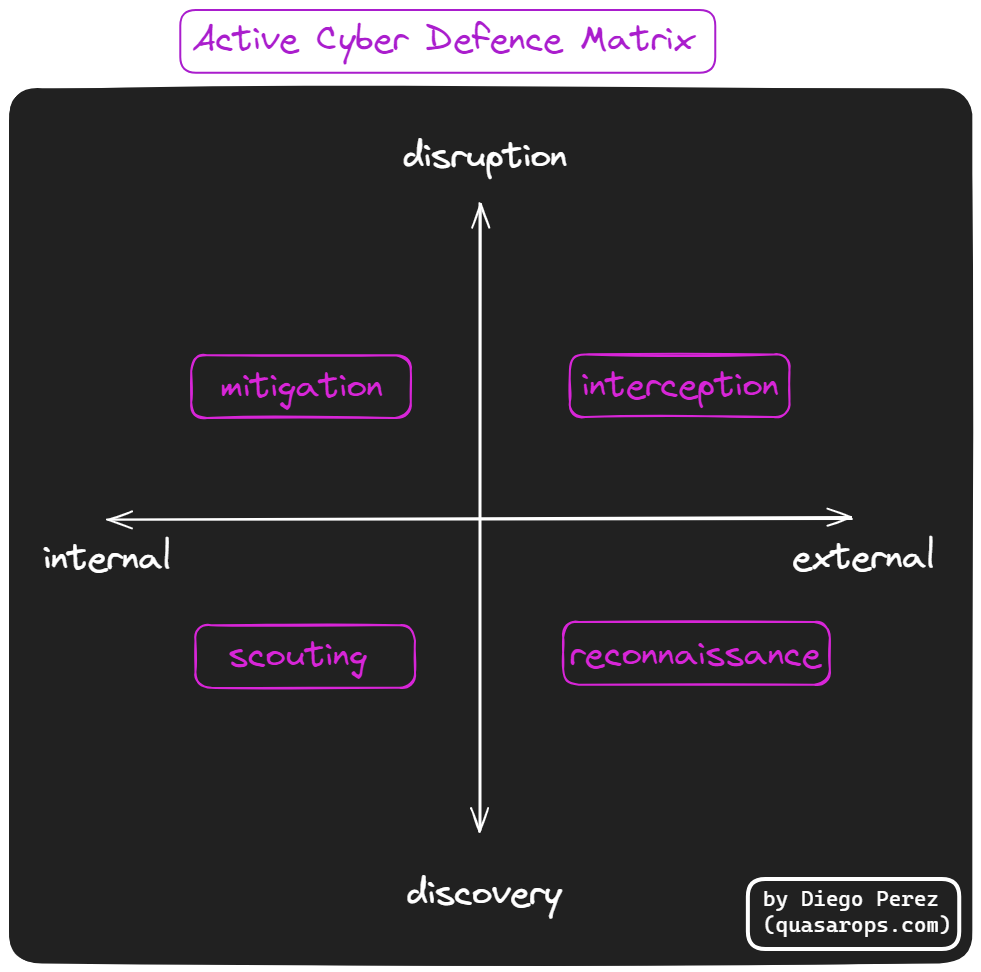
Operating within the adversarial engagement space, Active Defence encompasses two primary modes of engagement: discovery, focused on learning, observing, and detecting threats to gain insight; and disruption, centred on interception, containment, and eviction to neutralise threats. These two modes of engagement intersect with two other primitives that refer to the space, domain, or territory of engagement: external and internal.
The external territory designates everything outside your network perimeter, this includes not only the famous “threat landscape” or what is happening “out there” but also your business’s digital footprint that sits outside your direct network control (think user applications, ads, supply chain, vendor services, etc.). The internal territory designates all the digital systems inside your network. We could also add physical security considerations, but I will leave that for another time.
This approach shifts the security posture from simply reacting to actively positioning your assets and operations for predictively engaging threats.
Active Defence is more than what the industry currently thinks it is about, namely, cyber deception. Deception is but one of many strategies to enact active defence in cyber operations.
What I described above gives us the following matrix:
Constraining the Engagement Space: Active Defense and the "Unknowns" Challenge
Active Defense Operations, by emphasizing proactive engagement, directly addresses the challenge of “unknowns” by shifting from a purely reactive to a threat-led posture. As you know, I don’t like the term “unknown unknowns”, simply because it’s an empty concept. As Nassim Taleb puts it, one cannot systematize, formalize, and program randomness. People talk about “unknown unknowns” when, in reality, they are thinking and referring to “known unknowns” or “unknown knowns”, which are less insurmountable and void-like ideas.
It’s better to simply talk in terms of “unknowns”, that’s it, single word. Because the truth is we are referring to uncertainty. We want to understand the likelihood of something and the impact it may carry. True “unknown unknowns” have an entropy of 1 (or say 100%), absolute randomness. What this implies is that in the face of absolute random events, you have very little power to influence the outcomes.
But security is about influencing outcomes.
While absolute randomness remains unquantifiable, active discovery within both internal and external engagement spaces does reduce the scope of uncertainty.
Active discovery is about intentionally delving into the noise, generating purposeful disruption.
This is precisely what we want to enact by engaging penetration testers and red teamers. They don't passively wait for vulnerabilities to be revealed; they actively probe APIs, networks, and systems, intentionally creating "noise" (e.g., sending malformed requests, attempting exploits) to observe the responses. This "purposeful disruption" allows them to map the attack surface, identify weaknesses, and reduce the initial high entropy by transforming unknowns into known vulnerabilities. Each successful probe, each identified misconfiguration, shifts the odds, making their subsequent actions more targeted and effective, ultimately increasing the likelihood of a successful breach or data exfiltration.
By actively mapping and understanding your external digital footprint and threat landscape, as well as your internal network, organizations constrain the engagement space, mitigating uncertainty and enabling more effective threat modeling.
This proactive approach, focused on both learning and disruption, builds resilience by anticipating and neutralizing threats before they manifest as catastrophic "unknowns", ultimately fostering a security posture that prioritizes continuous adaptation and operational continuity.
The Learn-Act Cycle and Why Reactive Models Fail.
There are two main actions in cyber defence: you either learn or you act.
Think OODA.
Effective cyber defense hinges on the strategic integration of learning and action. Traditional security paradigms, limited to reactive mitigation, operate within a singular action-oriented quadrant (upper left in our matrix).
This approach inherently precludes the critical acquisition and operationalisation of intelligence, resulting in a static and ultimately vulnerable posture.
Active Defense is a cyclical dynamic process: discovery, the intelligence, data and exposure gathering phase, and disruption, the active and reactive operational response. Discovery reduces uncertainty by actively probing and analyzing the threat landscape, while disruption either neutralizes identified threats (when you find yourself under a malicious cyber attack) or injects benign payloads via red/purple/pentest to make systems behave in non-intentional ways and reveal (discover) vulnerabilities.
By linking these phases, Active Defense operationalises continuous learning, enabling adaptive responses that outpace adversarial evolution. Reactive models, devoid of this feedback loop, remain fundamentally incapable of achieving sustained resilience.
Sustained Cyber Resilience
Resilient systems, as defined by NIST, transcend mere recovery; they embody the capacity to anticipate, withstand, adapt, and evolve. This aligns directly with the Active Defense paradigm, which emphasizes a continuous learn-act cycle guided by strategic positioning of assets and resources.
Here is the catch, though: you may be able to withstand and recover from an attack or two, but can you do it consistently?
Allow me the easy play of words: how resilient is your resilience?
Traditional reactive security models, with a high emphasis on the “Protect” and “Respond” NIST domains, inherently lack the adaptive capacity necessary for resilience.
Concepts like diversity, realignment, and unpredictability, as outlined in NIST SP 800-160, Volume 2, are operationalised within Active Defense through continuous monitoring, contextual awareness, and adaptive response. For instance, diversity reduces single points of failure, while realignment ensures security measures are aligned with evolving mission needs. Unpredictability, while seemingly random, can disrupt adversarial reconnaissance and attack planning. Unpredictability can be achieved by implementing strategic approaches like cyber deception.
Just as a biological system adapts to environmental pressures, a resilient cyber system, informed by active intelligence and operationalised through continuous learning and action, evolves to maintain essential functionality, even under persistent adversarial pressure.
So, how resilient are your cyber operations?