A Year in Review: The Tales of a Cyberscout in 2024
From Threat Research Frameworks to Cyber Operations
Zetabytes of Ideas
And just like that, we concluded another full cycle around the sun.
A lot was written in 2024 by the inhabitants of this online metaverse: rivers of ink as a common Spanish saying goes. It’s crazy to think that data creation in 2025 is predicted to reach an astonishing 181 ZB.
In this vast ocean of data, my musings are barely a drop within a drop.
Life happened. I wasn’t able to write as much as I would have liked last year, a situation I hope to remediate in 2025.
I’m grateful for all my readers, and those of you who sent so many DMs and engaged in interesting conversations. Some of the most engaging dialogues I’ve had in the last 12 months happened with people that were new to the field, or looking for orientation towards a flourishing career.
In this article, I will share the central ideas of all the writings from 2024, which I hope some of you have found insightful.
Key ideas shared in 2024
When looking at the articles I wrote last year, the volume has been low in terms of quantity. However, I think the aggregated volume of ideas shared was massive.
I think the central topic that drove my efforts can be summarised as follows: how can we extract meaningful information from threat intelligence so that it can drive proactive cyber defence and uplift security controls?
It sounds simple, but if it were, why is it so difficult for many organizations out there to truly build structural and situational awareness driven by threat intelligence?
These two types of awareness, structural and situational, were introduced in the Cyber Defence Matrix by Sounil Yu. Sounil traces a difference between activities that happen left of boom and right of boom. A “boom” is an undesirable event that occurs between PROTECT and DETECT, a disruption to regular business operations operated by a cyber threat.
To build awareness of any type, you need the ability to convert data into information, the latter into knowledge and this, finally, into impact.
This is easier said than done.
As T. S. Eliot put it:
Where is all the knowledge we lost with information?
In my career, I’ve observed many different ways of structuring threat intelligence to inform structural and situational awareness, but in most cases, I’ve seen two wrong approaches that fundamentally undermine the success of your threat intelligence, threat hunting, detection engineering and incident response efforts:
The Rube Goldberg Trap. Operational chokepoints driven by poor harvesting and delivery of threat-related information and a limited understanding of what threat intelligence can do for you. This leads to over-engineered functions or aspects of your cyber operations, resembling Rube Goldberg Machines that introduce unnecessary complications and deliver very little value.
The Spherical Cow Trap. Threat Intelligence’s function in the business is structured to solve a problem that (a) doesn’t address the real problems the business should be solving and (b) introduces new problems in downstream processes due to its inefficiency. This happens because of an oversimplified idea of how information is produced and consumed in cyber operations. You are operating with a model of how your function interacts with the system which is fundamentally wrong. It is a clear example of a disconnect between business needs and technical solutions.
Last year, I tried to propose different solutions to this problem. I was obsessed -and still am- with how to drive meaningful progress (as opposed to naive progress lacking orientation) around the mining, utilization and refinement of threat intelligence for detection engineering, hunting and cyber deception.
The above took on the more generic shape of the R1D3 Framework (Research, Discovery, Disruption and Development) inspired by the ideas previously shared in aimod2.com.
So 2024 was for me a year to mature the ideas I’ve laid out since 2020, which started with asking myself what are the core principles that drive successful Incident Response and Digital Forensics teams.
Let me summarize very briefly the articles written last year. I hope you’ve enjoyed them ;)
R1D3 Threat Driven Research Pipeline - Part 1
In R1D3 Threat Driven Research Pipeline - Part 1, we focus on the first phase (Research) of the RIDE Active Defence Framework, emphasizing the importance of efficient research in threat intelligence, specifically extracting meaning from unstructured data like reports and summaries to improve security controls. The article introduces a research data pipeline with steps for collecting, classifying, and analyzing threat information, using Microsoft's report on Volt Typhoon as an example.
R1D3 Threat Driven Research Pipeline - Part 2
In R1D3 Threat Driven Research Pipeline - Part 2, we explore the "Analysis" phase of our framework. The article covers entity and relationship extraction, linking these to your specific environment, and deciding whether to investigate further. This process transforms raw threat data into actionable information for active defence.
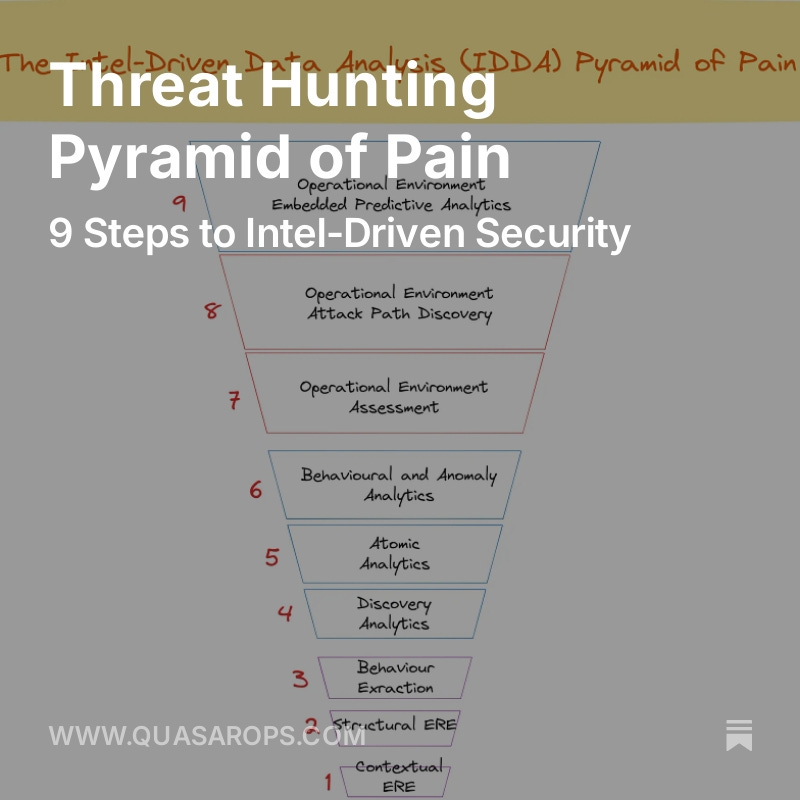
The Threat Hunting Pyramid of Pain
The Threat Hunting Pyramid of Pain presents a novel approach to threat hunting and analysis called the Intel-Driven Data Analysis (IDDA) Pyramid of Pain. A nine-step process, starting with understanding the context of a threat, extracting key indicators and highlighting the importance of assessing the organization's own environment, including its attack surface, vulnerabilities, and security controls. Finally, it advocates for proactive defence by simulating attacks and building predictive models to anticipate future threats.
Cyberops as Git Pipelines
In Cyberops as Git Pipelines, we ask ourselves what would it look like if your cybersecurity operations pipeline functioned like a Git repository. Each team acting as a branch, merging their insights and actions into a "main" pipeline to drive real-world impact. We propose a "Git-inspired" approach to scalable cyber operations.
Oh, you noticed?
In case it wasn’t already obvious, yes, I changed from Ghost to Substack. There was no point in me forking out significant $$$ each month to maintain a free site. Substack allows me to share my ideas for a much lower fee and comes with an entire ecosystem that is quite interesting.
Writing is a hobby for me. I need to reduce friction to the minimum in order to focus on what matters most: unfolding ideas about resilient cyber systems, active defence and tech leadership.
I encourage you to check your Spam or Junk folder for any newsletter emails from the Tales of a Cyberscout (quasarops.com) that may have been misplaced by the gods of the metaverse
So what’s next man?
Keep an eye out for the exclusive Subscriber Chat I will kick off any time soon. A place for the Tales of a Cyberscout readership to share ideas and contribute to discussion topics.
I wish you all a wonderful 2025 and flourishing careers!